The rise of phishing during weeks of emergency: best practices and authentication to defend yourself

Cybercriminals always try to exploit tough times to convey their frauds, be it phishing, scams, or other types of abuse. The weeks we’ve been experiencing are indeed no exception.
What’sthe basis for this “momentum” of cybercriminals? They hope that areception filter will loosen up during these weeks, which is a baselesshypothesis, and that the recipientswill become morevulnerable and inclined to interact with the communications in theirinbox.
This second hypothesis is actually founded, as shown in our previous blog post. There, we reported how March opening rates and clicks were significantly higher than the averages for the rest of the year.
Wehave always been at the forefront of the fight against all kinds of abuse bye-mail by adding to the discussion and doing everything in our power to preventthe spread of fraudulent communications. Today, we want to give you a moreprecise idea of what phishing attempts look like, plus some indicationson how to stand up againstcybercrime.

From developing integrations to strategic support, from creating creative concepts to optimizing results.
MailUp has built solid, global relationships with ISPs and blacklists over the years. We all constantly share information on policies, practices, and issues. Anyone wishing to help MailUp provide a better service or to collaborate is welcome. Please, write us at abuse@mailup.com.
Phishing cases reported during the current emergency
We’vebecame aware of numerous abuse attempts, even if they didn’t affect the MailUpinfrastructure. These can be grouped into two macro categories:
1. Phishing attempts disguised as institutional communications. You will find several examples of such attempts in this post.
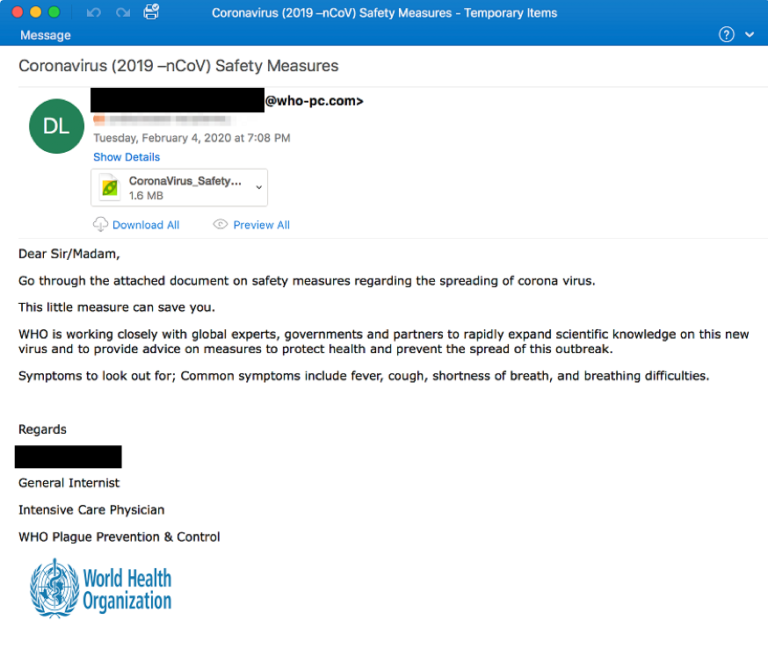
2. Malware transmitted via a site similar to the Johns Hopkins University infection map.
Our SpamHaus friends summarized the general situation in this blog post.
Best practices to defend yourself against phishing
Albeitwith the awareness thatphishingcannot be fully resolved, let’s glance at best practices that can discourage (if not even prevent) this type of problem:
- Always try to make yourbrand identity recognizable in the messages you send. This may seemtrivial but it is not: those who do phishing, even if they try to replicateyour logo, can never 100% copy all the details that are part of your digitalidentity.
- Do not use “lookalike” or “cousin” domains in your official communications. If recipientscan expect communications from domains such as “brandname-email.com”,then they could mistakenly consider legitimate domains that aren’t (e.g.“brand-name-email.com” or “brandname-mail.com”). Always useyour domain and, if you would like to differentiate the flows, adopt subdomains(email.brandname.com), as indicated in the best practicespublished by the M3AAWG.
- Be aware of which domain is used in the DKIM signature and, if possible,try to align this domain with the one you use as the sender.
- Publish an appropriate DMARC policy (quarantine / reject) to safeguardthe reputation of your domains. Although attackers will continue to use similardomains, their chances of deceiving recipients will be significantly reduced.Further, this will make you ready to make the best use of the news of theE-mail Marketing ecosystem (BIMI, for example) in the future.
Areyou wondering what the DKIM, DMARC, and BIMI abbreviations mean? Let’s shedsome light on this.
Authentications: what they are and what they’re for
DKIM
DKIM(acronym for DomainKeys Identified Mail) is an e-mail authentication system. Byadding an encrypted signature, itmakes receivers able to verify whetherthe message has been altered, at least in its fundamental fields, betweensending and receiving.
Namely,our public key DKIM must be added to your web domain settings and a specific signature is added to allthe e-mails we send for you.
The encryption of this signature is based on some elements of each sent e-mailand is, therefore, unique for each message. When analyzing your e-mail, thereceiving mail server will decrypt the signature with the aforementioned publickey. It will then generate a newhash string based on the same elements. The e-mail will be consideredDKIM-authenticated, if there’s a match between the decrypted signature and thenew hash string. Here’s a DKIM signature example:
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; s=transactional; d=mailup.com;
h=From:To:Date:Subject:MIME-Version:Content-Type:List-Id:List-Unsubscribe:Message-ID; i=news-it@mailup.com;
bh=eFMbGLxi/7mcdDRUg+V0yHUTmA1F4EXExVBQxIxBr2I=;
b=ra3pGFHHvCr9OZsm9vnOid……..Yj00/+nTKs=
If the message has a valid signature (i.e., not manipulated), then the signingdomain—identified by the d=tag—will communicate who you are to the receiversthat will then handle the mail accordingly. The reputation assessment systemsof the main Mailbox Providers haveincreasingly given weight to this identifier compared to others (e.g. the IP).Nowadays, some providers (such as Gmail) allow for monitoring the reputationbased on this identifier. In short, this has become a mandatory element for communication delivering.
DKIMconfiguration occurs through the configuration of DNS records. This is not adifficult operation. However, it’s impossible to have a standard personalizedsignature for all customers precisely because having a DKIM signature is mandatory.
Forthis reason, all major ESPs use one or more signatures of their servicedomains. This grants a best practice compliance but produces a sort of “shared reputation” amongall customers in that cluster. Now, this may not be optimal in certain cases(especially if some customers have much larger volumes or perform lower thanothers).
For this reason, the MailUp platform offers the chance to use your own domain as a DKIM signature. We are available to all customers through our deliverability consultancy for those who seek further information or require help in configuring DKIM records.
Protect your mailings
Not a MailUp customer yet? Contact us
DMARC
Essentially,DMARC allows a domain owner, who is also the sender of e-mail messages, to aske-mail providers not to deliverunauthorized messages that appear to come from their domain. As you mayhave guessed, this is a useful mechanism to prevent phishing and spoofingattacks.
Froma technical point of view, DMARC (Domain-based Message Authentication,Reporting & Conformance) is a DKIM and SPF authentication-based system thathelps the receiving servers (e.g. Gmail, Yahoo, Libero, etc.) know what to do when a message can’t beauthenticated. To do so, it allows the e-mail sender to publish a “policy” to instruct the receivingservers on how to manage any authentication problems. Further, DMARC providesa reporting mechanism forthe actions taken, based on the policy. This way, it coordinates the results ofDKIM and SPF and specifies under which circumstances the sender e-mail address,which is often visible to the final recipient, can be considered legitimate.
Financial institutions and other companies subject to phishing and spoofing attacks can best protect themselves by implementing a DMARC policy.
Incorrectly configuring a DMARC record can have a substantially negative effect on deliverability, not only for e-mails sent through us but also for all communications sent by a DMARC-enabled domain (e.g. employees’ e-mails to external receivers). Meaning, we recommend that you consult a deliverability expert for a DMARC policy proper implementation.
BIMI
BIMI(Brand Indicators for Message Identification) represents the near future of E-mail Marketing.
Currently,it has been adopted only by the Verizon Media Group (in other words, Yahoo!& AOL) but with a commitment by Google. BIMI is a vendor-independent standard that allows brands to display their verified logo in the recipient’sinbox for fully authenticated e-mails (DMARC).
BIMIencourages major brands to adopt adequate e-mail authentication, particularlyDMARC, when they send mass messages to consumers. Senders who commit toimplementing DMARC are rewarded with the display of their logo.This enhances both recognition and trust.
In summary
Asyou may have noticed, our advice is to take control ahead of time. We’re surethat this series of implementations is destined to bear fruit in terms of abuse protection and sending quality.
In fact, just sending is not enough. Spam, outdated databases, and wrong settings can reduce the delivery rate and damage your brand’s reputation. To protect yourself from risks you can count on the Deliverability Suite services. Its customized configurations and constant monitoring will always keep your deliverability safe.